Android Enterprise Solutions
Contact us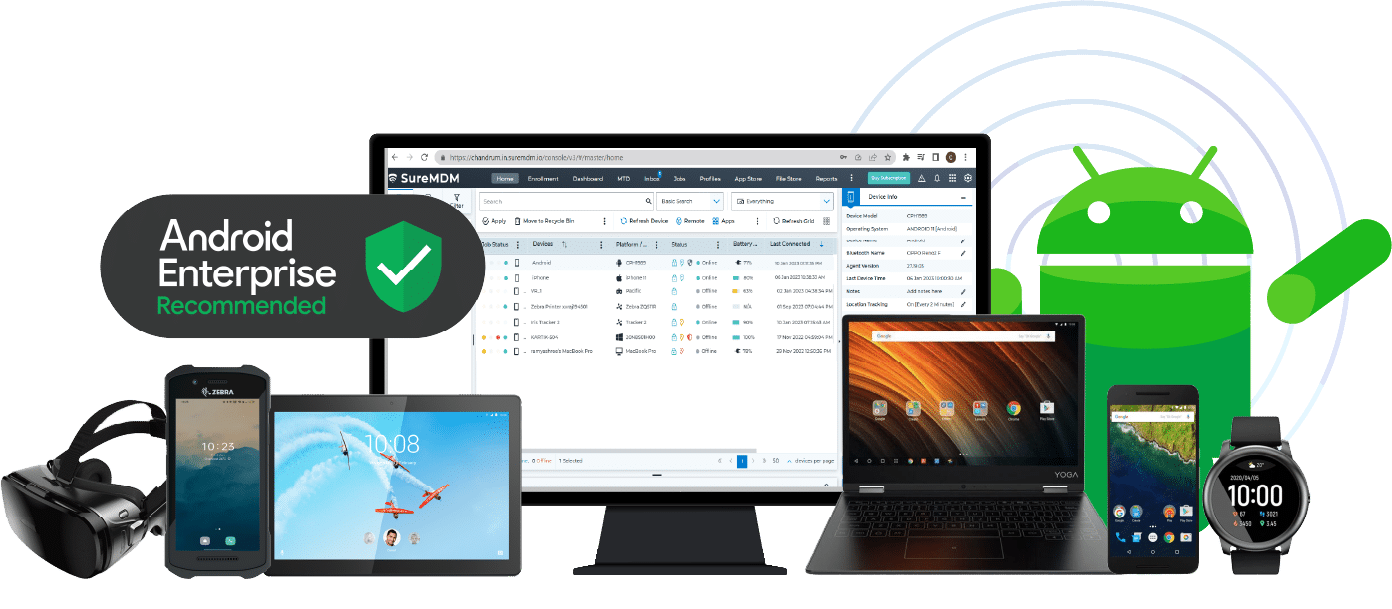

Mobile Application Management
Contact us

IT Service Management
Contact us

Software Asset Management
Contact us

Endpoint Protection / IT security
Contact us

Software Distribution
Contact us

Inventory Management
Contact us